So today I was working at a site that has a single Exchange 2010 server that forfills all the Exchange roles (I know….) which happened to fall on its ass.
First thing I did was check the Exchnage services which were in a state of “starting” which is never good and then I went to the registry and found:
MSExchange ADAccess, EventID 2141
Process STORE.EXE (PID=2996). Topology discovery failed, error 0x8007077f
MSExchange ADAccess, EventID 2142
Process MSEXCHANGEADTOPOLOGYSERVICE.EXE (PID=1760). Topology discovery failed, error 0x8007077f
Here’s a few screen shots:


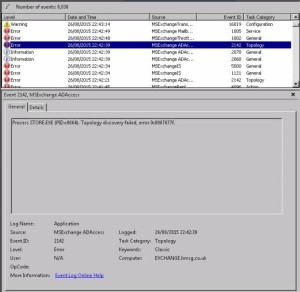
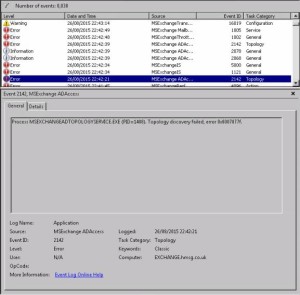
As well as a few more related to AD.
After some investigation I found out that a new DC in a new site had been created for some DFS replication amongst other things.
As the system could start the Microsoft Exchange Active Directory Topology service (until it failed and is restarted by dependent services), Exchange’s other services were also triggered, leading to almost indefinitely restarting services as configured in their corresponding service recovery actions sections.
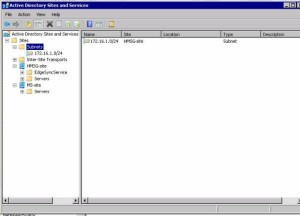
So next up is to look at Active Directory Sites and Services:
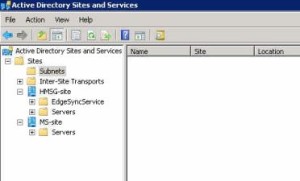
And as you can see from the screen shot the subnets are missing, which is going to cause issues as the new DC is on a different subnet.
When Exchange can’t determine in which site a computer belongs, the function DSGetSiteName, used to retrieve the current site, returns an error 1919 0x77f (ERROR_NO_SITENAME) which in turn kills off Exchange. You can test this by running nltest /dsgetsite in a command prompt or by having a look at HKLM\System\CurrentControlSet\Services\Netlogon\Parameters\DynamicSiteName.
To solve the issue you can do any of the following:
- Making the site association static using a registry key, which isn’t a best practice. If you must, set registry key HKLM\SYSTEM\CurrentControlSet\Services\Netlogon\Parameters\SiteName(REG_SZ) to the desired site name;
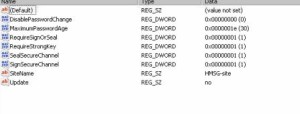
- Adding proper subnet definitions;
- Remove the new site.
Finally give Exchange a bounce and BOOM.
Note that the NetLogon service determines site association membership at startup and every 15 minutes. The Microsoft Exchange Discovery Topology service maintains this information by caching the information in the msExchServerSite attribute of the Exchange server object, in order to reduce load on active directory and DNS. Therefore, you might need to wait or restart Microsoft Exchange Discovery Topology if you want to renew site association membership.







